Source code Obfuscator
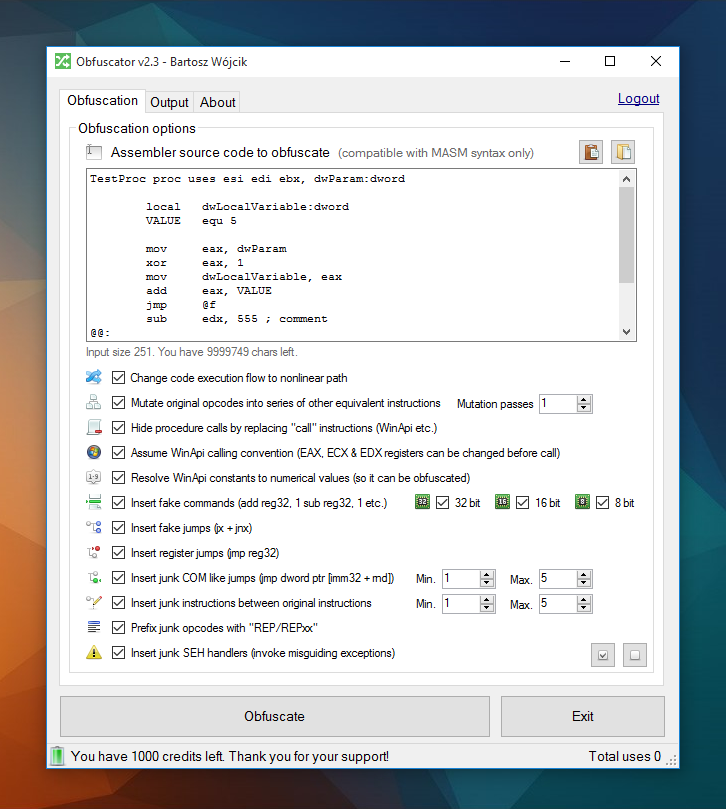
Obfuscator is a tool to obfuscate assembler source code. Obfuscation protects source code against cracking and reverse engineering analysis.
Source code obfuscation
Obfuscation is the process of transforming input source code into a protected version to prevent cracking and reverse engineering analysis.
If you're writing assembler code and you want to protect your work from decompilation and reverse engineering, or just want to make it as hard as possible to analyze, you might want to try Obfuscator.
Obfuscator features
- it's OS independent
- you can use Obfuscator as a dedicated Windows application, or an online interface & or using our Web Api (e.g. from a PHP script)
- MASM syntax only, processing of
@@labels, detection of local variables, constantequvalues, and numbers in different formats (hex, dec) - changing code execution flow (non linear code path) - it's useful against all kinds of debuggers, analysis of such code is very hard
- mutation of original instructions into series of other equivalent opcodes - Obfuscator can mutate both arithmetic and logical opcodes
- hiding of direct calls to functions (including WinApi calls)
- inserting garbage opcodes between real instructions (so called junks)
- inserting fake instructions between real ones, 32/16/8 opcodes are generated
- inserting fake exceptions between real code (SEH frames)
- resolving of WinApi constants to numerical values (so it can be obfuscated)
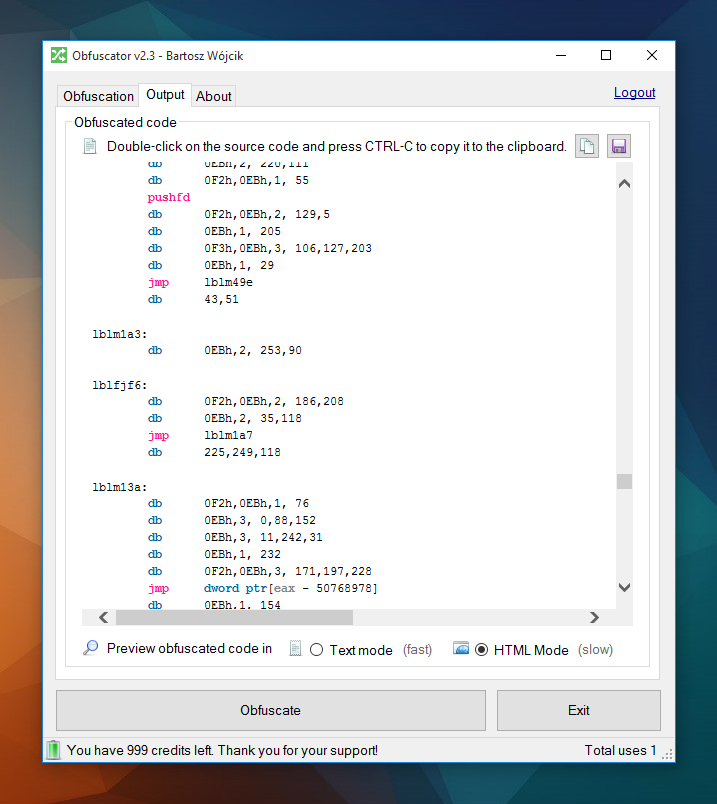
Obfuscation example
See how it works: compare both original.exe and obfuscated.exe files. If you don't know how to do this, you might want to read my articles about reverse engineering.
obfuscator20_example.zipv2.0 | ZIP Archive | 39 kBCommand line
Obfuscator comes with an additional command line interface.
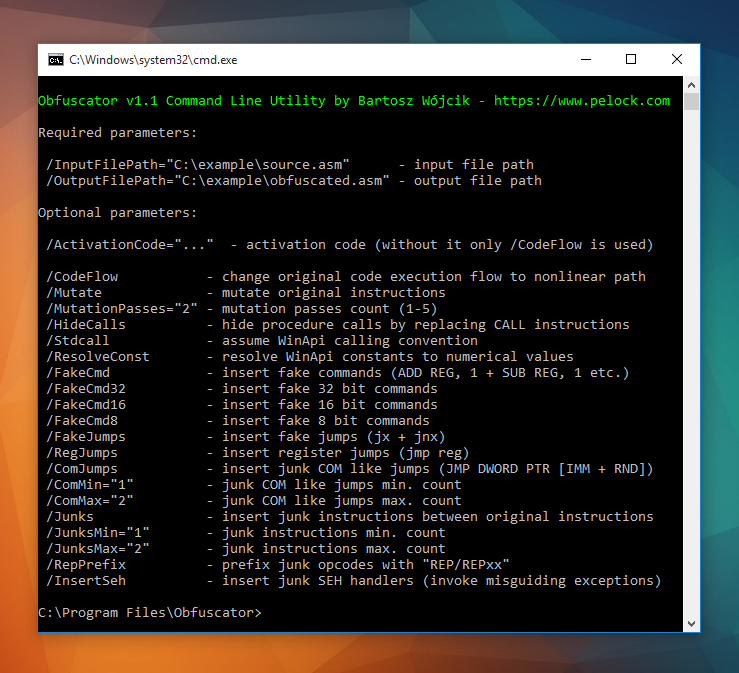
This allows you to integrate obfuscation into your build process or any other batch operation.
Any questions?
If you would like to ask me about Obfuscator, or something's not clear, mail me, I'll be happy to help you.